In this blog post I'm going to explain how overall response of a XACML policy changes with different rule combining algorithms. We are going to use WSO2 Identity Server 3.2.3 as XACML engine.
Let's consider following policy.
1. The first rule's effect is deny. According to this rule, anyone who belongs to "dev" group is NOT allowed to read the personal information record of Jerry.
2. The second rule says that a person who is at least 5 years scenior to Jerry can read Jerry's personal information record.
So what will be the final outcome of policy evaluation if Tom (who belongs to "dev" group) is 7 years senior to Jerry ? Should we totally ban Tom from reading those records or should we allow him to read them considering about his experience and seniority ?
This is a decision which can be handled/changed through policy based on the actual requirement.
1st scenario :
Regardless of their experience, we want to prohibit people belonging to "dev" group from reading Jerry's personal information. In this situation we need to use above policy with "deny-overrides" as rule combining algorithm.
For following request, XACML engine will return "Deny" as the result.
2nd scenario :
We need to allow read permission to anyone who is at least 5 years senior to Jerry.
In this case role should be neglected if above requirement is fulfilled.
We can use the same policy after changing the rule combining algorithm to permit-overrides.
To change the rule combining algorithm, click "Edit" in Home -> Entitlement -> Administration. Then change the rule in " Edit Policy Element" page and save the policy.
Note : You have to enable the policy every time you edit it.
Now send the same request (given in 1st scenario) again. "Permit" will be returned as the result.
3rd scenario :
Now let's see about the next rule combining algorithm. i.e. first-applicable. Here the first applicable rule will be picked up from the set of rules defined in the policy.
To change the rule combining algorithm, go to "Edit Policy Element" page by following the instruction I've given above and change the algorithm to first-applicable.
In our sample policy, there are two rules. First rule evaluates to deny and second one evaluates to permit decision.
Keep the policy as it is (only change the rule combining algorithm) and send the request given in scenario 2. You'll receive "Deny" as the result because the first applicable rule (for the request) evaluates to deny.
Now go to "Edit Rule Elements" page (Entitlement -> Administration -> Edit -> Next -> Next) and change the order of rules as shown below.
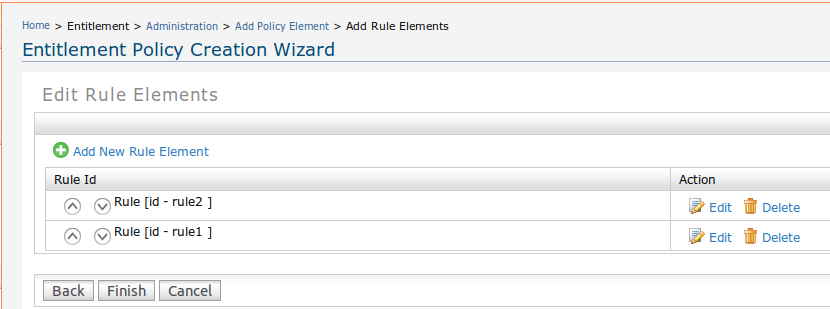
If you send the same request again, the result will be "Permit".
You can see that by changing the order of the rules in policy, you'll be able to change the final decision.
In this blog post, I tried to explain the behavior of different rule combining algorithms using one policy. In the next post, let's see how policy combining algorithms can affect the policy decisions.

I wanted to know if you could inform me on how to use identity server as an xacml engine for an application that is hosted on an external server (tomcat or glassfish for example) what would i need to change or configure in identity server
ReplyDelete